Access Management API
Connected App Examples
Connected Apps feature provides a framework that enables an external application to integrate with the Anypoint Platform APIs through OAuth 2.0 and OpenID Connect. It enables you to use secure authentication protocols to control an application's access to user data. For more information, see Connected Apps.
OAuth framework specification describes several grant types for acquiring access tokens for different use cases. The ones that are supported by Anypoint Platform to use with the connected apps are outlined below with examples.
Authorization Code & Refresh Token
The flow for using Connected Apps with the authorization_code grant type is as follows:
1. Creating a connected app
POST /accounts/api/connectedApplications HTTP/1.1
Host: anypoint.mulesoft.com
Authorization: Bearer $UserAccessToken
Content-Type: application/json
{
"client_name":"GitProxy",
"grant_types":["refresh_token", "authorization_code"],
"redirect_uris":["https://example.com/"],
"scopes":["profile","offline_access"],
"public_keys":[],
"audience":"internal"
}2. Authorizing the app to act on the user's behalf
Using the client ID retrieved from the previous step, users can verify the information in the Authorize App interface and grant access to the application.
GET /accounts/api/v2/oauth2/authorize?client_id=<client_id>&scope=profile%20offline_access&response_type=code&redirect_uri=https://example.com&nonce=123456
Host: anypoint.mulesoft.com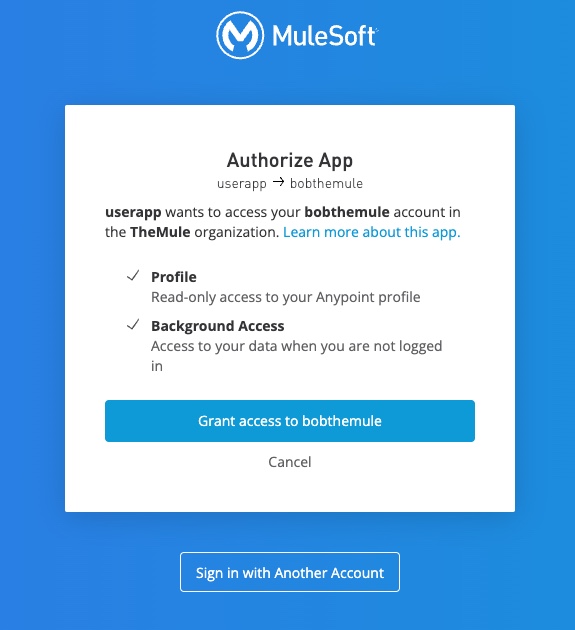
3. Retrieving the access token
POST /accounts/api/v2/oauth2/token HTTP/1.1
Host: anypoint.mulesoft.com
Content-Type: application/json
{
"client_id":<client_id>,
"redirect_uri":"https://example.com",
"client_secret":<client_secret>,
"grant_type":"authorization_code",
"code":<code_retrieved_from_step2>
}Sample response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"access_token" : <access_token>,
"refresh_token" : <refresh_token>,
"expires_in" : <60_minutes_in_seconds>,
"token_type" : "bearer"
}4. Accessing the API using the retrieved access token
GET /accounts/api/profile HTTP/1.1
Host: anypoint.mulesoft.com
Authorization: Bearer $ConnAppAccessTokenSample response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"id" : <connected app owner id>
"createdAt" : <connected app owner created at>
...
}5. Retrieving new access token using refresh token
The following example shows the structure of a token request given a pre-existing refresh_token:
POST /accounts/api/v2/oauth2/token HTTP/1.1
Host: anypoint.mulesoft.com
Content-Type: application/json
{
"client_id" : <client_id>,
"client_secret" : <client_secret>,
"grant_type" : "refresh_token",
"refresh_token" : <refresh_token_retrieved_from_step3>
}Sample response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"access_token" : <access_token>,
"refresh_token" : <refresh_token>,
"expires_in" : <60 minutes in seconds>,
"token_type" : "bearer"
}Note: To receive an id_token in the token response, openid scope is required.
Password Grant
The following is an example structure of password grant type request:
POST /accounts/api/v2/oauth2/token HTTP/1.1
Host: anypoint.mulesoft.com
Content-Type: application/json
{
"grant_type" : "password",
"client_id" : <client_id>,
"client_secret" : <client_secret>,
"username" : <username>,
"password" : <password>
}Sample response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"access_token" : <access_token>,
"expires_in" : <60_minutes_in_seconds>,
"token_type" : "bearer"
}JWT Bearer Grant
Example flow for using Connected Apps using JWT Bearer grant type:
1. Creating a Connected App with JWT Bearer grant type
POST /accounts/api/connectedApplications HTTP/1.1
Host: anypoint.mulesoft.com
Authorization: Bearer $UserAccessToken
Content-Type: application/json
{
"client_name" : <name_of_the_app>,
"grant_types" : ["urn:ietf:params:oauth:grant-type:jwt-bearer"],
"public_keys" : [<public_key>],
"redirect_uris" : ["https://example.com/"],
"scopes" : ["profile","offline_access"],
"audience" : "internal"
}2. JWT Token Exchange
Creating an assertion, that is a signed JWT using the privateKey. A sample payload with the claims could be as follows:
- iss: application's clientId
- sub: version|idp_id|username|firstname|lastname|email|externalgroups
- aud: token endpoint
{
"iss" : <client_id>,
"sub" : "v2|0b132ac3-d8f6-44b2-953c-2333df741f05|jsmith|john|smith|jsmith@gmail.com|[community]"
"aud" : "https://anypoint.mulesoft.com/accounts/api/v2/oauth2/token"3. Retrieving the access token
POST /accounts/api/v2/oauth2/token HTTP 1.1
Host: anypoint.mulesoft.com
Content-Type: application/json
{
"grant_type" : "urn:ietf:params:oauth:grant-type:jwt-bearer",
"assertion" : <assertion_from_step2>
}Sample response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"access_token" : <access_token>,
"expires_in" : <60_minutes_in_seconds>,
"token_type" : "bearer"
}Client Credentials Grant
The following is a sample structure of a client_credentials grant type request:
POST /accounts/api/v2/oauth2/token HTTP 1.1
Host: anypoint.mulesoft.com
Content-Type: application/json
{
"client_id" : <client_id>,
"client_secret" : <client_secret>,
"grant_type" : "client_credentials"
}Sample response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"access_token" : <access_token>,
"expires_in" : <60_minutes_in_seconds>,
"token_type" : "bearer"
}