Product Entitlement Customer Experience API
Authentication
Your requests must be authenticated before you can make API calls. Our API is secured using OAuth 2.0 Bearer Token authentication. You can use an interactive authentication method or a non-interactive authentication method. For both methods, the outcome is a JSON Web Token (JWT).
The JWT gives your application permission to access the Product Entitlement Customer Experience API.
If you make a successful request for a JWT, the token is returned to you in the following format where access_token is the JWT:
{
"access_token": "{your_access_token}",
"token_type": "Bearer",
"expires_in": "3600",
"refresh_token": "{your_refresh_token}",
"id_token": "{your_id_token}"
}The following image shows a blurred example of a JWT decoded using jwt.io:
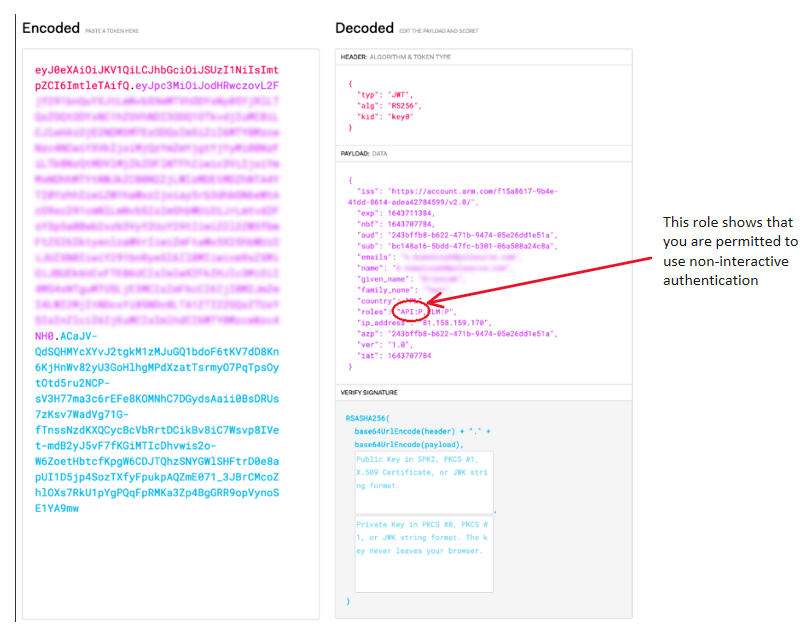
Microsoft Azure Active Directory B2C backs Arm Account for authentication. For that reason, you must authenticate with Microsoft to obtain tokens to make API calls. This authentication process requires specific parameters which are described in detail in the Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials article. The parameters that are applicable to the Product Entitlement Customer Experience API, are as follows:
tenant: TBD
client_id: TBD
grant_type: password
username: Your Arm account email address.
password: Your Arm account password.
scope: TBD
client_secret: TBD
client_assertion: TBD
Non-interactive authentication
This form of authentication requires you go through an initial approval process with Arm. If approved, non-interactive authentication allows you to make API calls from a server without user interaction to obtain an access token.
Contact your Arm Partner Program Manager (PPM) and make a request to be allowed to use non-interactive authentication. To perform this type of authentication, you must also register for a new Arm account at https://developer.arm.com/register and provide this email address to your PPM.
You must keep the credentials for this account secure within your organization. This account can only be used for the API and is not able to log into other Arm systems.
Every 180 days you must verify your account is active and change your password using a link sent out by email. For this reason, we recommend setting up a new shared inbox for this account.
Interactive authentication
This form of authentication is quick to set up and is suited for testing, experimenting, and making direct API calls.
Before you begin
You require your Arm account email address and password.
Procedure
- Go to https://developer.arm.com/downloads/token.
- Enter your Arm account email and password.
- Save the token you receive.