Tangoe OAuth API
home
OAuth for REST APIs
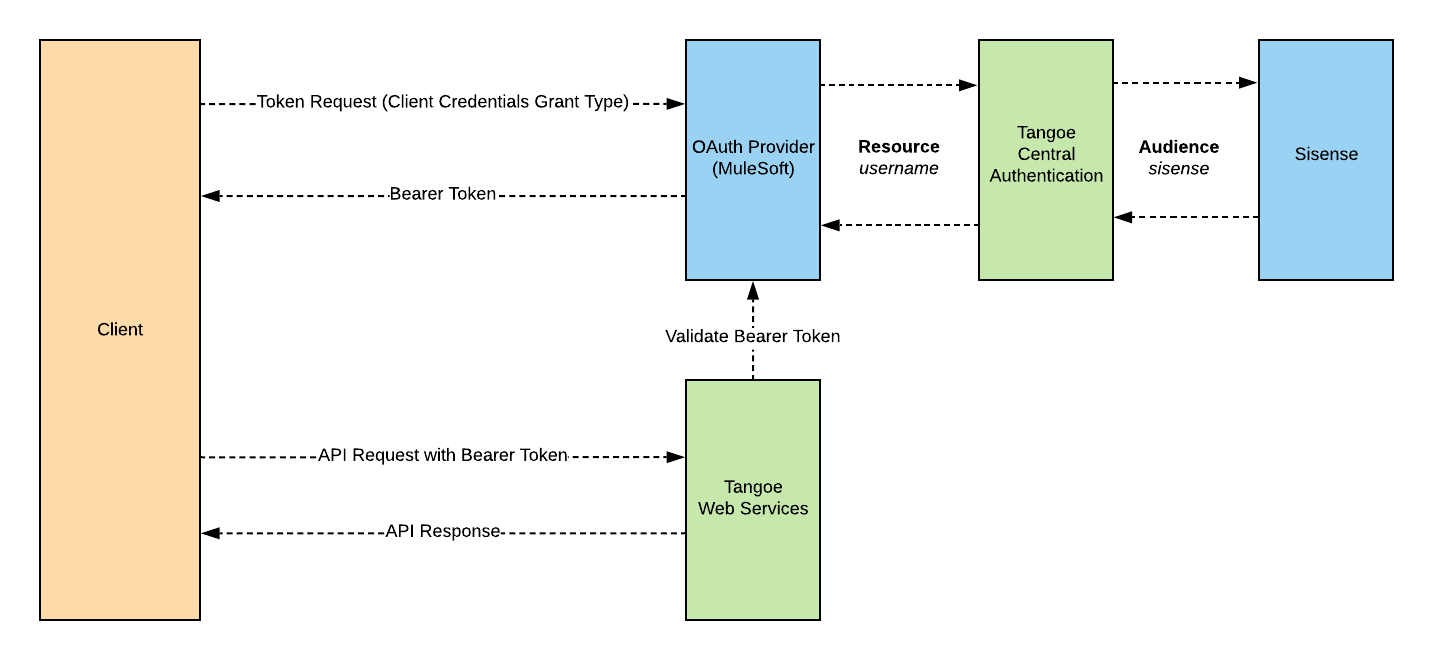
OAuth is the primary authentication protocol for many of the Tangoe REST APIs.
This OAuth library currently supports authenticating into the following Tangoe applications.
Central Authentication
Enterprise
Sisense
The typical OAuth flow requires a client to request a client_id and client_secret from Tangoe. Authorization requests are done through the client_credentials grant type within OAuth. If a token is required for a resource (user), a username header must also be passed with the authorization request.
OAuth URLs
| Environment | URL |
|---|---|
| Production | https://tangoe-oauth.us-e1.cloudhub.io |
| Development | https://tangoe-oauth-dev.us-e1.cloudhub.io |
Requesting a Bearer Token
Requesting a bearer token requires the client to send the following headers to the /access_token endpoint in the OAuth API.
| Header Key | Description |
|---|---|
| client_id | The tenant specific Client ID that has been provided by Tangoe. |
| client_secret | The Client Secret associated with the specific Client ID. This should be treated as a password and protected on the client side. |
| grant_type | The grant type to be used in the authorization request. This should be set to client_credentials. |
| username | The email address of the user for which to scope the token. This is used in conjunction with the audience header when providing user specific tokens for applications. This is only required if the token is for Enterprise or Sisense. This must be present when setting an audience. |
| audience | The audience represents the application for which the token is being requested. This is only required if the token is for Enterprise or Sisense. This must be present when setting a username. Accepted values are enterprise, sisense |
| Content-Type | The content type of the payload being sent with the token request. This is only required if the audience is set to sisense. |
| scope | This value is currently not used, but may be used in the future to scope authorizations to a particular permission set (READ, WRITE, etc). |
Examples
Requesting a General OAuth Token
curl --location --request POST 'https://tangoe-oauth-dev.us-e1.cloudhub.io/access_token' \
--header 'client_id: 16b8d3bf-54d3-47b4-873f-df17f0c3a512' \
--header 'client_secret: 491872ae-6f76-432d-827d-1baa9b8840cc' \
--header 'grant_type: client_credentials' \Requesting an Enterprise OAuth Token
curl --location --request POST 'https://tangoe-oauth-dev.us-e1.cloudhub.io/access_token' \
--header 'client_id: 16b8d3bf-54d3-47b4-873f-df17f0c3a512' \
--header 'client_secret: 491872ae-6f76-432d-827d-1baa9b8840cc' \
--header 'grant_type: client_credentials' \
--header 'username: john.doe@tangoe.com' \
--header 'audience: enterprise' \Requesting a Sisense OAuth Token
curl --location --request POST 'https://tangoe-oauth-dev.us-e1.cloudhub.io/access_token' \
--header 'client_id: 16b8d3bf-54d3-47b4-873f-df17f0c3a512' \
--header 'client_secret: 491872ae-6f76-432d-827d-1baa9b8840cc' \
--header 'grant_type: client_credentials' \
--header 'username: john.doe@tangoe.com' \
--header 'audience: sisense' \
--header 'Content-Type: application/json' \
--data-raw '{
"app_name": "TeleCom",
"customer_code": "TNG",
"email": "john.doe@tangoe.com",
"role": "admin",
"groups": ["group1", "group2"],
"first_name": "John",
"last_name": "Doe",
"cube_name": "CUBE_DATA",
"cube_alias": "TeleCom Main Cube",
"scopes": [
{
"table_name": "location_dim",
"column": "country",
"datatype": "text",
"members": ["value1", "value2"]
},
{
"table_name": "cost_center_dim",
"column": "name",
"datatype": "text",
"members": []
}
]
}'OAuth Token Response
The token request will respond with a JSON payload that will include the access token, if authorization was successful. The payload will also contain additional data elements as outlined below.
| JSON Key | Description |
|---|---|
| access_token | The Access Token to be used in future API requests. |
| token_type | The type of token returned. This dictates how the token should be used in future requests. This will almost always be Bearer. |
| expires_in | The time stamp in which the token will expire. This value is a Unix Timestamp in seconds. |
| scope | The scope of the token such as READ, WRITE, etc. This will often return an empty value. |
| access_uri | If the token is to be used in a specific exchange, a formatted URI will be returned for ease of usage. Currently, this value is only returned if the audience is set to sisense. |
Example Response
{
"access_token": "2x7TMxy54x_fSObtzr_ca-TDA3t73II2fbjlAiX8RBxHMJfFnGg3q2cA_pBHP2Q3DHJJ_krFEe0P6UtPgho7pQ",
"token_type": "Bearer",
"expires_in": 86400,
"scope": null,
"access_uri": null
}Validating a Bearer Token
An application can validate a bearer token using the /validate endpoint in the OAuth API. This endpoint should only be used to validate tokens that are not resource specific (i.e., were not requested with a username header). Validation of JWT bearer tokens should be done by parsing and validating the JWT on the application side using the shared secret.
A validation request requires the token to be sent as a Bearer token in the Authorization header, just as it would be used in other APIs. the response will contain information about the validity of the token.
Example Request
curl --location --request POST 'https://tangoe-oauth-dev.us-e1.cloudhub.io/validate' \
--header 'Authorization: Bearer 82ivRzrIrMa0npVkdHk3jZRqq2wzm5Kl7oS6LdajlCQgIUb4oZ9VRqtMIf4OYZr1vRsaOjKtzliiQt5tUW6PIA'The response from a validation request will contain several attributes about the token, including the tenant.
| JSON Key | Description |
|---|---|
| client_id | The Client ID associated with the token. |
| scope | The scope applied to the token such as READ, WRITE, etc. |
| expires_in | The expiration time of the token. This value is a Unix Timestamp in seconds. |
| customer_code | The Tangoe designated customer code associated with the tenant for which the token was generated. |
Example Response
{
"client_id": "bd029261e9f330c82dbc3be0c44a14ab5fa761f90e484a6f63f219c4c5a5e461",
"scope": "",
"expires_in": 86374,
"customer_code": "TNG"
}Revoking a Bearer Token
In a good practice to invalidate the bearer token once you have finished using it. To do this, you can revoke the token from the OAuth provider.
Example Request
curl --location --request POST 'https://tangoe-oauth-dev.us-e1.cloudhub.io/revoke_token' \
--header 'Authorization: Bearer QaHVHpQyrLDrfl1vdZpIeu9iEdWXfFguOaFTMNOTHN4DHZ6ELLpFaeuZnsbESIBaZ2O1CKjjZugXnKvNRzRBpw'Example Response
{
"message": "Token revoked."
}